An Identity Governance and Administration (IGA) platform serves as the central authority for defining and enforcing access policies. However, its effectiveness is entirely dependent on its ability to communicate with the diverse landscape of target systems—applications, databases, and infrastructure—where digital identities and permissions are managed. This bridge is established and maintained by connectors.
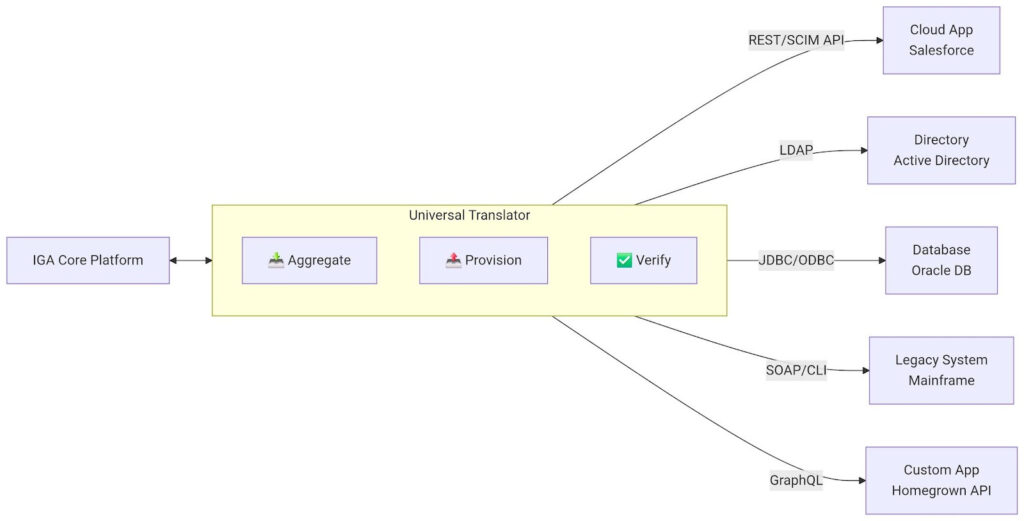
A connector functions as a specialized software component that translates the IGA platform’s generalized commands (e.g., “assign role”) into the specific protocol and data format required by a target system (e.g., a specific API call or LDAP modification). It bridges the gap between abstract policy and technical implementation, enabling automated, auditable, and consistent governance. Without connectors, an IGA platform would be unable to perform its core functions of visibility and control over the enterprise IT environment.
The Core Functions of a Connector
Connectors facilitate a continuous cycle of governance through three primary functions: aggregation, provisioning, and verification.
1. Aggregation (The “Read” Function)
Aggregation, also known as reconciliation, is the process of pulling identity, account, and entitlement data from a target system into the IGA platform. This foundational function builds and maintains a centralized, unified view of access rights across the organization. This data is essential for:
- Visibility and Reporting: Providing a single source of truth for who has access to what.
- Access Certifications: Supplying managers and asset owners with the data needed to conduct periodic access reviews.
- Policy Evaluation: Detecting access that violates established policies, such as Separation of Duties (SoD).
2. Provisioning (The “Write” Function)
Provisioning is the process of executing commands from the IGA platform onto the target system to grant, modify, or revoke access. Triggered by identity lifecycle events (e.g., joiner, mover, leaver), provisioning automates access changes. The connector translates a logical request from the IGA platform into the precise technical operations required by the target system, such as:
- Create: Creating a new user account.
- Update: Modifying user attributes or adding/removing entitlements (e.g., roles, group memberships).
- Delete/Disable: Deactivating or deleting an account upon user departure to remove access promptly.
3. Near-real-time Verification (The “Check” Function)
After a provisioning action is sent, a robust connector performs verification. It queries the target system to confirm that the requested change was successfully applied. This closed-loop reconciliation is critical for maintaining data integrity and providing a reliable audit trail, ensuring that the state recorded in the IGA platform accurately reflects the permissions in the target system.
Connector Implementation Models
Because no two enterprise environments are alike, connectors are available in two primary models:
- Out-of-the-Box (OOTB): These are pre-built, vendor-supported connectors designed for common commercial and enterprise systems (e.g., Microsoft Entra ID, Salesforce, SAP). They are generally preferred for their rapid deployment, reliability, and ongoing maintenance by the vendor.
- Custom: For homegrown applications, legacy systems, or niche platforms without OOTB support, custom connectors must be developed. They extend governance to all critical assets but require an initial development investment and ongoing maintenance by the organization.
The Connector Framework: Enabling Scalable and Customized Integration
Modern IGA platforms include a Common Connector Framework (CCF) to standardize and accelerate the development of custom connectors. Rather than building from scratch, developers use the framework to apply business-specific logic to pre-built templates that handle common protocols (e.g., REST/SOAP, SCIM, SQL).
- Aggregation Rules: Custom logic can be used to transform inbound data into a consistent format for the IGA platform. This includes normalizing data (e.g., mapping location codes to full names) or correlating low-level permissions into a single, business-friendly entitlement.
- Provisioning Rules: Custom logic can translate a single IGA directive into a complex series of operations required by the target system. For example, a “Create User” event can trigger a rule that executes multiple, sequential API calls to build an account, assign a profile, and set initial security parameters.
The Evolution to Intelligent Connectors
The integration of Artificial Intelligence (AI) and Machine Learning (ML) is transforming connectors from procedural intermediaries into intelligent agents that enhance governance.
Key AI-Driven Capabilities:
- Intelligent Aggregation and Role Mining: AI algorithms can analyze aggregated entitlement data to discover hidden access patterns, identify orphaned accounts, and recommend optimized business roles based on usage and clustering.
- Predictive and Risk-Based Provisioning: ML models can predict the access a new user will likely require based on peer analysis, accelerating onboarding. They can also assess the real-time risk of an access request and trigger step-up authentication or additional approvals before the connector executes the change.
- Self-Healing and Adaptive Operations: An intelligent connector can autonomously handle transient failures (e.g., by retrying a command if a target system is temporarily unavailable) and detect API changes in SaaS applications to flag potential integration failures before they occur.
- Behavioral Analytics (UBA): By analyzing logs and usage data, AI can establish a baseline of normal user activity. Deviations from this baseline can trigger an alert, an automated access review, or a temporary suspension of access via the connector, enabling a shift from periodic to continuous, risk-based access verification.
Key Considerations for Advanced Connectors: The efficacy of AI-driven IGA depends on high-quality data. Organizations must also address challenges related to model explainability for auditors, the potential for perpetuating historical bias, and the added complexity of implementation.
Conclusion
Connectors are a foundational component of any IGA architecture. They are the essential infrastructure that translates policy into practice. The evolution of connectors—from standard OOTB integrations to customizable frameworks and, ultimately, to AI-enhanced intelligent agents—is critical for enabling organizations to build a proactive, secure, and efficient identity governance program capable of addressing the challenges of the modern digital enterprise.
Disclaimer: The views expressed in the content are solely those of the author and do not necessarily reflect the views of the IDPro organization.
About the author

Mr. Anant Wairagade is an internationally recognized Senior Cybersecurity Engineer and independent researcher with a Bachelor of Engineering in Computer Science. His expertise lies in a niche and highly visible field within the software industry: enterprise-scale identity and access management, with a particular emphasis on cloud security, zero-trust architectures, and the application of artificial intelligence. His significant contributions to this field, demonstrated through his publications, technical program committee work, and impactful achievements at American Express and other major corporations, have earned him a reputation as an expert in a specialized area.