
The concept of Non-Human Identities (NHIs) has become a defining topic in Identity and Access Management (IAM). This article introduces the issue, explains why it matters, and previews the two key perspectives — lifecycle and access — that subsequent pieces will examine in depth.
In combination, the three articles (“Understanding NHI,” “Lifecycle of NHIs,” and “Access and Governance for NHIs”) outline a practical framework for managing non-human identities with the same discipline we apply to people, without losing sight of their fundamentally different nature. In a future post, I will dive into the specific IAM issues around Agentic AI.
Introduction
The hottest topic in IAM these days is not AI, nor is it RBAC versus ABAC; it’s NHI, or Non-Human Identities. And there’s a good reason for that: many LinkedIn influencers post their opinions about NHI, there are blogs and webcasts, management solutions and tools are popping up, and it’s hot.
And rightly so, NHI is important because while there may be 8 billion humans on this planet, there are 10 times as many non-humans living on the digital planet. A tenfold increase in actors and resources in need of access and access control. In our field of expertise, we need to know who has access to what, and we almost know how to manage that (no, we don’t, but that’s a different topic). But managing access for non-human identities is not clear. And that really is a challenge, because non-human identities are already performing more transactions than humans can ever imagine, such as machine-to-machine communications, robotic automation processes (RPA), devices, scanners, and cameras, as well as car park barriers, etc.
And yet, the most common denominator is that there seems to be no consensus on how to handle this topic. Are we talking about non-human identities or non-human accounts? Does an NHI need access, and if so, to what, and perhaps more importantly, why? How do we cope with keys and tokens? Where do they come from? Is there a lifecycle for the identity and for the access tokens?
So, there is plenty of space for yet another blog about NHI, and I would like to describe the Access topic. And some of the Identity views that may exist. (I will share some links to IAM definition documents at the end of this article.)
Why NHI Matters Beyond the Hype
What makes the NHI debate more than a passing trend is that it touches core governance: ownership, accountability, and sustainability. To manage NHIs properly, we first need to understand how they live and how they act.
Lifecycle — How NHIs Come to Exist
Just like human identities, NHIs have a lifecycle. Somehow, they come to exist, they have a life and then they are destroyed. The following illustrates this principle.
For human identities, the HRM processes are the governing processes. Joiner–Mover–Leaver (JML) is the core model. Every Join, Move, or Leave event will be evaluated for the identity and access management consequences. If an actor joins an organisation, a digital identity is created, and one or more accounts or usernames are assigned to this actor. Moving within the organisation (new dept, new manager) will result in a re-evaluation of permissions. And when leaving, all permissions will have to be revoked and licenses terminated, to prevent the abuse of identities and identity theft.
For non-human identities, a different process is the governing process, not the JML processes. These processes are not HR processes. NHIs don’t apply for a job, nor do they drop from the sky. Instead, the governing process here is the Change Management process, and its registration happens in a Configuration Management Database (CMDB). As a further clarification, the digital identity lifecycle of non-human accounts, as defined in IDPro (see references below), is shown:
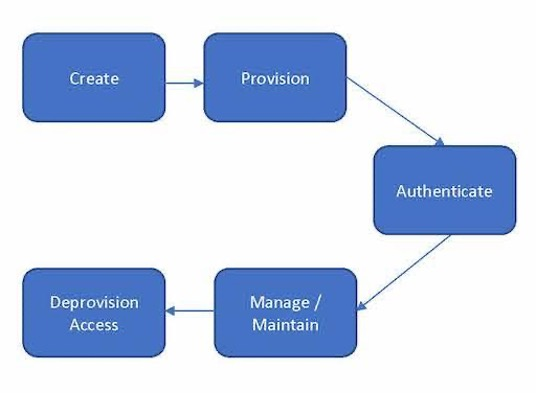
Figure 1: NHI lifecycle
This contrast shows why managing NHIs in HR-driven IAM tools is ill-fitting. In other words, we cannot approach the non-human identities in the same way we do with the human ones. The existence of NHI is more the result of Change Management rather than employment events, and their records belong in the CMDB, more so than in HR systems. More on that in the next article on Lifecycle Management for NHI.
Access — How NHIs Interact and Perform Tasks
Access control for NHIs is two-sided. They consume access to do their work, but they also provide interfaces that others use. I’ll set the scene on this duality a little more below.
There are some interesting observations to be made about access control and NHIs. And missing these views leads to misunderstanding NHI Access Control and results in conflicting advice and practices. Access control and NHI’s have at least two different aspects: Access to the component and Access by the component. And these different views can be evaluated in this visualization:
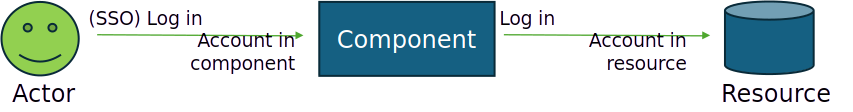
Figure 2: Access to and access by an NHI
In this illustration, an actor logs in to a component interactively. The actor has an account and authorisations to match. The component, in turn, logs into a resource, probably using a resource account and authorisations. Since the login is automated, the secret to logging in is probably configured in the component. The component could be an application, a camera, or a device.
These two views (Access to and by the component) are central to understanding NHI security. Without differentiating them, organisations blur responsibility and risk auditability gaps. For a deeper dive into this, have a look at [this article] on Access & NHI’s, which examines how these permissions are defined, granted, and controlled through the principle of least privilege.
From Theory to Governance
In short, NHIs are already here, performing countless actions on our behalf. Understanding them begins with recognizing that every non-human identity represents accountability, not just automation, and approaching it from the perspective that NHI management is more than just a technical discipline. It is about ownership and governance across change and access processes. To set up that governance, organisations must recognize where NHIs live in their architecture and assign accountability accordingly.
In two subsequent articles, I will focus on two topics that are close to my heart and that are often overlooked. First, there is the identity lifecycle, and second, the topic of access control. In combination, the three articles outline a practical framework for managing non-human identities with the same discipline we apply to people, without losing sight of their fundamentally different nature.
At the time of writing this article, further research is underway in the areas of RPAs (Robotic Process Automation, or bots) and Agentic AI. This will lead to more articles that will follow once presentable.
When read together, these insights form a coherent narrative: NHIs are neither employees nor users; they are governed components that perform defined tasks. They need identities, accounts, and authorisations. Yet, their management lifecycle and access patterns differ fundamentally from those of humans.
References
There are great resources that cover NHIs, but the two topics covered in this article are not clearly identified:
- https://sphericalcowconsulting.com/2025/01/13/understanding-nhis-key-differences-between-human-and-non-human-identities/
- https://www.csoonline.com/article/2132294/what-are-non-human-identities-and-why-do-they-matter.html
- IDPro: Non-human account management: https://bok.idpro.org/article/id/52/
- IDPro: Digital Identity Lifecylce: https://bok.idpro.org/article/id/31/
- https://www.linkedin.com/pulse/ultimate-guide-non-human-identities-lalit-choda-qc1ze/
- https://owasp.org/www-project-non-human-identities-top-10/2025/top-10-2025/
More online resources:
- https://www.linkedin.com/posts/boughtnotsold_agenticai-nonhumanidentities-identityorchestration-activity-7345598538136920064-5ONR
- https://www.linkedin.com/feed/update/urn:li:activity:7345598538136920064?commentUrn=urn%3Ali%3Acomment%3A%28activity%3A7345598538136920064%2C7345762368188002306%29&dashCommentUrn=urn%3Ali%3Afsd_comment%3A%287345762368188002306%2Curn%3Ali%3Aactivity%3A7345598538136920064%29
- https://www.linkedin.com/pulse/what-we-eliminated-accounts-torres-dur%C3%A1n-cisa-crisc-cige-cist-5uluc
Disclaimer: The views expressed in the content are solely those of the author and do not necessarily reflect the views of the IDPro organization.
About the author:

André Koot is principal IAM consultant at Dutch IAM consultancy and managed services company SonicBee (an IDPro partner). And member of the Advisory Board of IdNext.eu. He has over 30 years of infosec experience and over 20 years of experience as an IAM expert, acting as architect, auditor and program lead. For the last nine years he has taught a 4-day IAM training course. André contributes to the IDPro BoK as committee member, author, and reviewer.






